PKI Interoperability Models (February 2005)
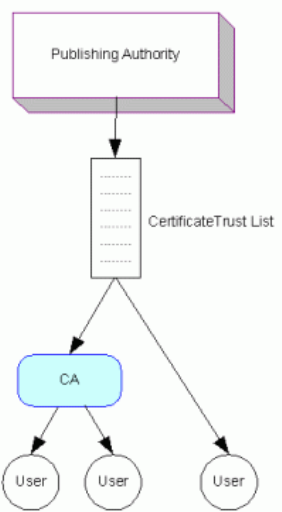
4.5. Certificate Trust List Model
The Certificate Trust List (CTL) is a list of CAs’ certificates from a trusted authority. The list itself is electronically signed to ensure its integrity. While CTLs are simple, they provide a very useful device for communicating trust and replace the need for the more complex process of cross-certification. They are employed in a wide range of different administrative structures, such as the cross-recognition model used by the Pan-Asian Alliance (discussed above).
Figure 8. Certificate Trust List Model
Trust lists have also given rise to the ‘browser’ model - the most widespread interoperable PKI by virtue of web browser applications (such as Internet Explorer, Netscape or Firefox). These browsers use a list of pre-loaded certificates from several dozen of the largest and most reputable CAs such as Verisign, RSA and Thawte. Almost all e-commerce websites such as www.ebay.com or www.hotmail.com display a certificate issued by those particular CAs. When a browser visits their site, their certificates are automatically recognised and the user has some assurance that the web site is from the organisation it claims to be.
From an inter-domain interoperability perspective, the CTL essentially replaces the cross-certificate pair... The key is that the relying party trusts the issuer of the CTL, which then allows the relying party to trust the CAs conveyed within the CTL. ... Like any of the other alternatives, acceptable practices and procedures are required in order for this mechanism to be a viable alternative for achieving inter-domain interoperability. Specifically, what constitutes a trusted CTL issuer and the criteria that the CAs must adhere to before they can be considered “trusted” must be established.[33]
In the feasibility study[34] for the EU IDABC project discussed below, a different model was suggested where each participating PKI domain – in this case, each EU Member State – would exchange CTLs of government-accredited CAs. This is essentially a cross-certification mesh model that uses trust lists instead of cross-certifications. It is a simple solution in a technical sense, but it retains the administrative and management complexity of the cross-certification model.
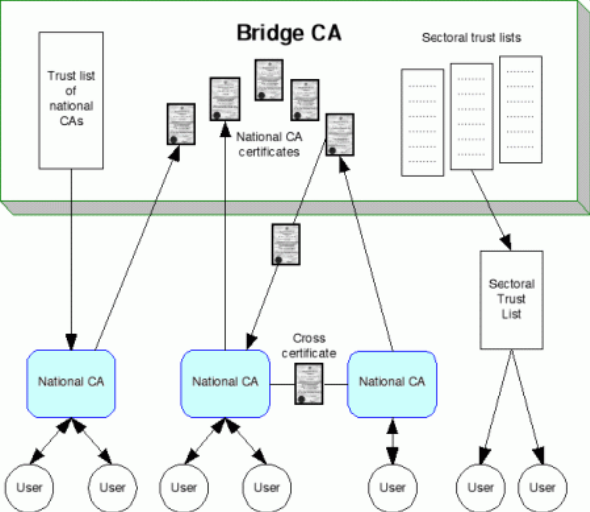
Certificate Trust List working example: The EU IDABC Bridge/Gateway CA
The EU IDABC Bridge/Gateway CA[35] (BCA) has proposed a model that uses the centralised administrative structure of a bridge, and distributes trust using both cross-certifications and CTLs.
The BCA will be operated by the European Commission itself. The focus of the project is to allow interoperability between the PKIs of EU governments and their agencies, and the model assumes in each Member State there will be a national CA that operates that government’s PKI. The BCA will bridge together each of these national CAs. It will perform a number of functions:
- It will publish a CTL of national CAs. Those national CAs can retrieve the list themselves and are free to add and subtract CAs from the list and republish it to their government’s users according to their own national preferences.
- It may also publish CTLs of CAs in particular sectors – for example, a list of CAs accredited to provide health certificates.
- It will cross-certify with each national CA and make that certificate available to other CAs to perform their own cross-certifications.
- It will provide a directory service listing each national CA and maintain a CA Revocation List and Certificate Revocation List.
- It is also suggested that the bridge might provide an OSCP (Online Certificate Status Protocol) service, to route requests to the appropriate CA to determine if a foreign certificate has been revoked.
- It will provide a test bed service to help new CAs ensure they are integrated correctly.
Figure 9. EU Modified Bridge CA Model
The feasibility study for this project[36] also considers the options for managing the variety of Certificate Policies (CPs) used by different CAs. It notes that the US Federal Bridge CA accepts the CPs as submitted by the CAs and maintains equivalence tables, allowing relying parties to make their own judgments about whether or not the CP provides a sufficient level of trust.
The EU study rejects this option, noting the administrative burden it would place on the BCA, and declares its preference for creating a limited set of standard CPs. Individual CAs could then be accredited to use these standard CPs by their national co-ordinating CAs. The individual CAs can combine the most demanding terms of their own policy stated on the certificate and the standard BCA CP to derive a set of procedures, usages and profiles that satisfy the BCA requirements as well as their own.
This EU project is still in a pilot phase, but it could be suggested that it represents the most mature theoretical approach to interoperability, taking lessons from the various international projects and adapting the best aspects of each model. At the same time it must be noted that it has the advantage of being placed in the tightly integrated and developed economies of the EU. Indeed, it is an expensive model with significant initial and ongoing costs, but provides a balance between the autonomy of its members and the efficiency of integration.
[34] Refer to footnote 6, page 31.
[35] Europa – IDABC, Bridge/Gateway Certification Authority, September 2004
<http://europa.eu.int/idabc/en/document/2318>.
[36] Refer to footnote 34, page 37.

![[2018 Global Cloud Computing Readiness Scorecard]](/public/ssi/pubs/pub_1.png)
 print this page
print this page sitemap
sitemap rss news feed
rss news feed manage email subscriptions
manage email subscriptions