 Projects
Projects
AEMO - Australian Energy Market Operator
- AEMO - Advice on cloud based identity (2013)
- AEMO - Identity and Access Management Architecture Strategy and Roadmap (2012)
![[ Galexia Dots ]](/images/hr.gif)
| |||||||||
![[ Galexia Dots ]](/images/hr.gif)
AEMO - Advice on cloud based identity (2013)
Galexia provided the Australian Energy Market Operator (AEMO) with options for implementing Single Sign-On (SSO) to external Software-as-a-Service (SaaS) applications. Our consultants performed an analysis of AEMO's authentication requirements, internal and external applications, and existing processes. We used our expert knowledge of cloud-based SSO technology vendors and solutions to select and cost the best approach, based on proven cloud identity design principles and best practices.
![[ Galexia Dots ]](/images/hr.gif)
AEMO - Identity and Access Management Architecture Strategy and Roadmap (2012)
Galexia delivered an Identity and Access Management (IAM) Strategy for the Australian Energy Market Operator (AEMO). Our consultants performed an analysis of AEMO's current state IAM business processes and technology, and determined the future state based on requirements and best practice. Galexia performed an IAM market review and technology evaluation that identified and costed the products most appropriate to AEMO. Leveraging the analysis and review, Galexia consultants provided an IAM Strategy and Roadmap for a 2-3 year period.
Our phased approach generates a number of staged outputs.
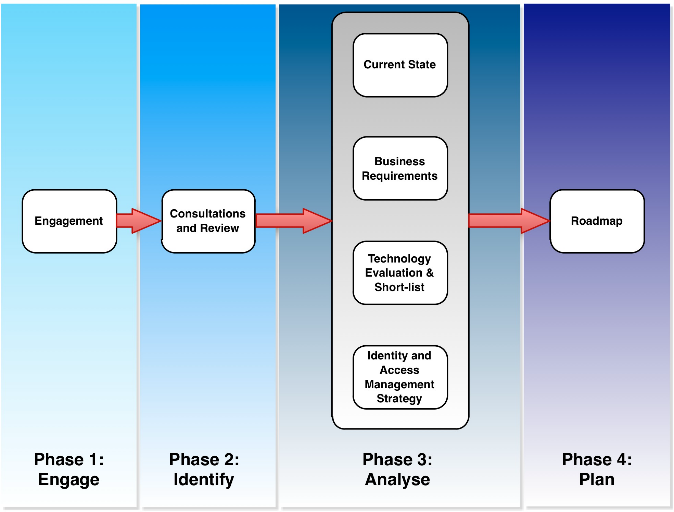
- Phase 1: Engage - Agree on the project scope and timetable, establish communication and collaboration mechanisms, and confirm on reporting requirements.
- Phase 2: Identify - Focus on identifying relevant inputs via stakeholder consultations and collection of other relevant materials.
- Phase 3: Analyse - Develop analysis and advice in four major documents:
- A Current State Analysis (Output 1), focusing on issues and gaps in current AEMO IAM processes and technologies;
- A set of Business Requirements (Output 2), based on analysis of materials collected in Phase 2;
- A Technology Evaluation (Output 3), comparing a number of vendor offerings across metrics relevant to the identified requirements; and
- An Identity and Access Management (IAM) Strategy (Output 4), a technology-neutral document setting out a broad vision, identifying key requirements and goals, and presenting a high-level architecture.
- Phase 4: Plan - Based on the recommendations and outcomes of the analysis, development of an Implementation Roadmap (Output 5) that includes scope, plan and timeline for proceeding with IAM implementation activities. This also includes recommendations regarding a vendor solution and estimated implementation costs. The Roadmap enables commencement of IAM implementation activities.
![[ Galexia Dots ]](/images/hr.gif)

![[2015 EU Cybersecurity Dashboard]](/public/ssi/pubs/pub_4.png)


 print this page
print this page sitemap
sitemap rss news feed
rss news feed manage email subscriptions
manage email subscriptions