Submission - Joint submission to the 2007 Review of the Electronic Funds Transfer (EFT) Code of Conduct to ASIC (May 2007)
Trusted Password Windows and Dynamic Security Skins
In their paper entitled The Battle Against Phishing: Dynamic Security Skins,[56] the authors discuss the development of an extension for the Mozilla web browser which implements two techniques to prevent spoofing of websites.
The first technique involves presenting the end-user with a ‘trusted’ window which is dedicated to the function of username and password entry. The user shares a secret (an image) with the browser and each time the user visits a website where they are required to enter a username and password, they are presented with the trusted window which contains the image. This makes it far easier for the end-user to detect when they have been presented with a spoofed window prompting them to enter their authentication credentials, since a spoof is unlikely to be able to display the image the user expects to see. A further advantage is that the user shares their secret with the web-browser rather than a server. This means that the user need not remember a different shared secret for each website where they need to log-in: the one image can be used for all websites. This reduced burden on the end-user perhaps reduces the likelihood of users lacking motivation to adopt the technology. However this implementation does not protect against spoof servers, since any website can instruct the browser to open the window.
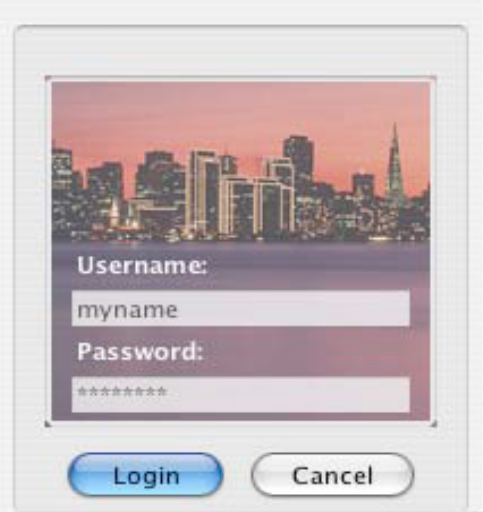
A trusted password window which displays a user’s secret image as the background
The second technique involves applying the Secure Remote Password Protocol (SRP) (discussed at page 52) to generate a ‘dynamic security skin’ that is displayed to the user on any authenticated web pages..
The authors’ plug-in extends SRP by using the hash values exchanged in the last part of the authentication process to enable both the server and client to independently generate an ‘abstract image’ or ‘skin’ using a special algorithm. If both parties have been successfully authenticated, the skins should match. The skin the browser expects to receive can be displayed to the user in the trusted password window. The server will correspondingly display the skin it has generated in any web pages it presents to the user. The user then simply needs to ensure that the skins match in order to ensure they are not interacting with a spoofed version of the website.
[56] Dhamija R and Tygar J D, The Battle Against Phishing: Dynamic Security Skins, Symposium On Usable Privacy and Security, July 2005, <http://cups.cs.cmu.edu/soups/2005/2005proceedings/p77-dhamija.pdf>.

![[2018 Global Cloud Computing Readiness Scorecard]](/public/ssi/pubs/pub_1.png)
 print this page
print this page sitemap
sitemap rss news feed
rss news feed manage email subscriptions
manage email subscriptions