Submission - Joint submission to the 2007 Review of the Electronic Funds Transfer (EFT) Code of Conduct to ASIC (May 2007)
SpoofGuard
SpoofGuard is an Internet Explorer browser plug-in developed to assist users in determining when they are visiting a spoofed website.[55] SpoofGuard works by examining web pages a user has visited and using a variety of criteria to calculate a score, known as a ‘spoof index’, for the website. If the index exceeds a threshold set by the user, SpoofGuard then warns the user that the site is likely to be spoofed. SpoofGuard uses the following techniques to calculate the index for a particular web page:
- URL Checks
If a URL for a web page contains suspicious elements (such as the use of IP addresses, ‘@’ symbols and the like), this means it is more likely the site is spoofed. Similarly, if the URL closely resembles (but yet slightly varies from) a well-known domain name or a domain name previously visited by the user (e.g. paypaI.com may be used instead of paypal.com), this increases the spoof index. - Image Checks
SpoofGuard maintains a database of well-known images (often these are corporate logos of well known organisations whose websites are likely to be the target of spoofing attempts) and their associated domains. So, for example, logos used by eBay are stored in SpoofGuard’s database with the domain-name association ‘www.ebay.com’. If a user visits a site that uses those images, but the domain name does not match the corresponding domain name in SpoofGuard’s database, this increases the probability that the site is spoofed (spoofed sites will often use the same images used on the real site in order to create a convincing spoof). Although spoofers could easily overcome this by making very slight modifications to the image before putting it on the spoofed site, this can be combated through the use of a hash function. Specifically, a hash function would allow SpoofGuard to store the hashes of images rather than the images themselves. The hash function works in such a way that minor modifications to an image will not result in a different hash being produced. This allows SpoofGuard to perform an image check even if an attacker has slightly modified an image compared with one used on the real version of the website.
The image check could however be circumvented if a spoofer divided the image into ‘slices’ that were placed alongside each other on the spoofed website. Although the slices would appear as one contiguous image to an end-user, SpoofGuard would treat each slice as a separate image and would thus be unable to match any individual slice with an image hash stored in its database. - Link Checks
SpoofGuard checks to see how many of the links on the web page actually work; if at least one-fourth of the links fail, the site is more likely to be spoofed. - Referral Checks
If the user has followed a hyperlink to reach another web page, SpoofGuard increases the spoof index if the referring page was one where the user may have been reading email (for example, hotmail.com). This is because it is possible the user may have been lured to the site by use of a phishing email containing a hyperlink to the spoofed site. - Outgoing Password Checks
SpoofGuard monitors the websites a user visits and maintains a database recording usernames and passwords, as well as the domain name where each username and password is typically used (for security purposes, the password is stored as a hash). If the user then visits a spoofed website and attempts to enter the same authentication credentials they have used at another website, SpoofGuard will detect this and warn the user that they are about to submit their password and username to a site that is different from the one they normally submit the credentials to.
This check could be defeated by an attacker breaking the password input field on the spoofed web page into multiple adjacent fields which appear as one single input field to the user. SpoofGuard would then be unable to perform a password comparison test.
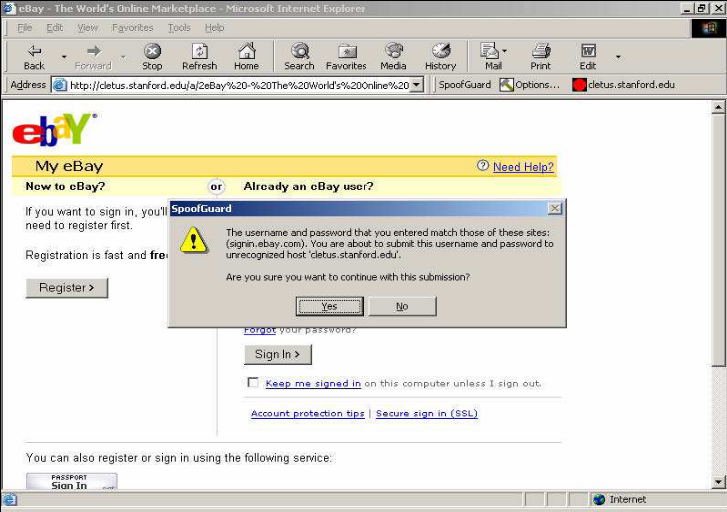
An example of SpoofGuard in operation
[55] Refer to Chou N, Ledesma R, Teraguchi Y, Boneh D and Mitchell J C, Client-side defense against web-based identity theft, Stanford University Computer Science Department, February 2004, <http://crypto.stanford.edu/SpoofGuard/webspoof.pdf>.

![[2018 Global Cloud Computing Readiness Scorecard]](/public/ssi/pubs/pub_1.png)
 print this page
print this page sitemap
sitemap rss news feed
rss news feed manage email subscriptions
manage email subscriptions