PKI Interoperability Models (February 2005)
4.3. Bridge CA Model
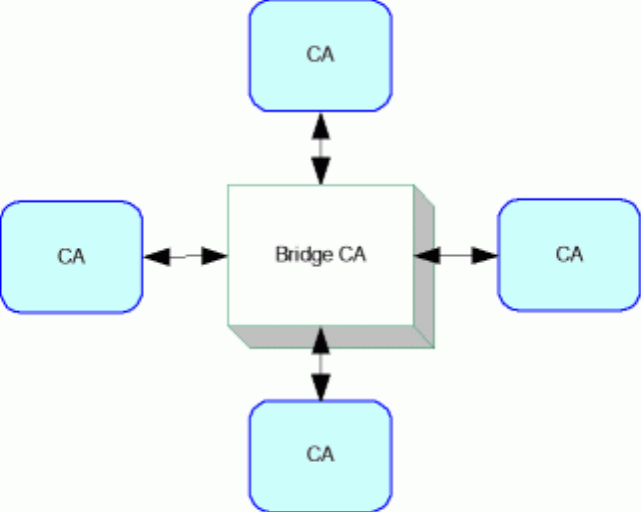
The bridge CA model is based around a central (bridging) CA which cross-certifies with each CA. It functions as a communication channel between each of the CAs.
This combines aspects of both the root model and the cross-certification model. It provides much of the administrative simplicity of the root model, because it only requires one pair of cross-certifications for each CA, rather than n2 certifications in a completely meshed system.
It also provides some of the flexibility of the mesh model because it is not conceived as imposing strict technical requirements on complying CAs. Nevertheless the bridge must set certain minimum standards for CAs to participate. For example, in the USA, the Federal Bridge CA specifies several different levels of assurance that a CA can be certified at. The bridge itself is focused on the task of providing interoperability.
Figure 5. Bridge CA Model
The bridge is an attractive model because it helps to centralise the management of interoperability problems in the one authority that can develop and promote the best solutions.
The bridge model allows for PKIs built using different models to be joined together in a single, interoperable network.
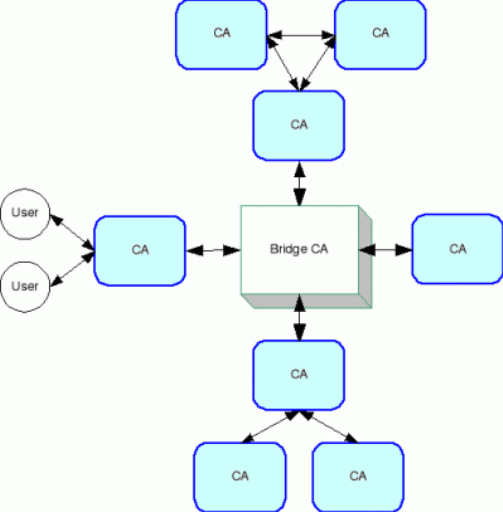
Figure 6. Expanded Bridge CA Model
This model also allows for bridge-to-bridge mutual cross-certification[21].
Bridge CA working example: US Federal Bridge CA
The bridge CA model has been pioneered in the US government’s Federal Bridge Certification Authority (FBCA) project[22].
In 2000, the Federal Chief Information Officer’s Council approved the FBCA Certificate Policy. This policy defines the FBCA as “an interoperability mechanism for ensuring trust across disparate domains.” In practice, this is a mix of the bridge CA model and elements of the cross-certification model:
Successful cross certification with the FBCA asserts that the Applicant Public Key Infrastructure (PKI) operates in accordance with the standards, guidelines and practices of the Federal Public Key Infrastructure Policy Authority (FPKI Policy Authority) and of the Federal PKI Steering Committee (FPKISC).For cross-certifications internal to the US Federal Government community, the FBCA Certificate Policy requires entities to sign a cross certificate Memorandum of Agreement (MOA) formally describing the terms and conditions of the cross certification. Cross certifications with non-Federal entities require the implementation of formal cross certification formal agreements between the US Government and the external entity. The details of these agreements may vary based on the nature of the external entity and its relationship to the Federal Government.[23]
The FBCA began operating in 2002. It appears to be working well, and there have been clear advantages from the development of this central organisation to coordinate and promote PKI interoperability. The bridged government departments include Defence, Treasury and NASA, and will soon include the Canadian Government, the Patents & Trademarks Office and the education sector’s own bridge (EDUCAUSE). One bridged application has used certificates issued by university faculties to authenticate employees of the National Institutes of Health.
The FBCA lets subscribing CAs develop their own policies and procedures, and then provides interoperability by managing equivalence tables for those policies. This allows relying parties to assess themselves whether or not the certificate provides the requisite level of trust.
The FBCA is an information system that facilitates an entity accepting certificates issued by another entity for a transaction. The FBCA functions as a non-hierarchical hub allowing the "relying party" entity to create a certificate trust path from its domain back to the domain of the entity that issued the certificate, and then to test that path using the requirements set forth in X.509 to determine whether the offered certificate contains the requisite level of trust to allow the transaction to consummate.[24]
Participation in the US Bridge is not mandatory, and parties in a PKI may use other methods to determine trust:
The FBCA does not add to and should not subtract from trust relationships existing between the transacting parties. At their discretion, agencies may elect to interoperate among themselves without using the FBCA. Those agencies that elect to do so may nonetheless employ levels of assurance that mimic those set forth in the FBCA CP.[25]
Several other sectors, such as the aerospace industry and the pharmaceutical industry, are establishing their own PKI bridges in the USA.
Bridge CA working example: European Bridge CA (EBCA)
The EBCA[26] is a privately run initiative of Deutsche Bank and Deutsche Telekom, and is a “pure” implementation of the bridge model, providing a central CA which cross-certifies with each CA domain. It has provided interoperability among a few major EU companies. However the European Commission has rejected this as too simple[27] because it does not include a mechanism for providing detailed information on CAs. It has modified this model in the newer IDABC Bridge/Gateway Project, discussed below under certificate trust lists.
[21] Federal Bridge Certification Authority, US Government PKI Cross-Certification Criteria and Methodology, October 2004
<http://www.cio.gov/fbca/documents/crosscert_method_criteria.pdf>.
[22] <http://www.cio.gov/fbca/>
[23] Federal Bridge Certification Authority, US Government PKI Cross-Certification Criteria and Methodology, October 2004
<http://www.cio.gov/fbca/documents/crosscert_method_criteria.pdf>.
[25] National Institute of Standards and Technology: Computer Security Resource Center, Federal Bridge Certification Authority
<http://csrc.nist.gov/pki/fbca/welcome.html>.
[26] <http://www.bridge-ca.org>
[27] Refer to footnote 8, page 125.

![[2015 EU Cybersecurity Dashboard]](/public/ssi/pubs/pub_4.png)
 print this page
print this page sitemap
sitemap rss news feed
rss news feed manage email subscriptions
manage email subscriptions